🔐 KEYSGUARD OWLWATCH — DAILY INTELLIGENCE BRIEF🦉
REPORTING WINDOW: JANUARY 19, 2026 |
OWLWATCH CYBER INTEL BRIEF |1,509 subscribers |Subscribe & SUPPORT
🔐 KEYSGUARD OWLWATCH — DAILY INTELLIGENCE BRIEF🦉
COFFEE: Hackers Weaponize Your Security Infrastructure — OWLWATCH🦉INTELLIGENCE
SPOTIFY: 🦉-OWLWATCH | Podcast on Spotify
Executive Summary
Tonight’s threat posture is defined by rapid exploitation pressure on widely deployed enterprise platforms (Windows, email security, monitoring/SIEM) and a steady rise in AI-assisted fraud and social engineering. The operational risk is not limited to endpoint compromise; attackers are actively targeting the security stack itself (email gateways, monitoring) to gain privileged execution, erase visibility, and accelerate lateral movement. Immediate priorities: patch verification, management plane exposure reduction, and targeted hunts for tunneling/log clearing behaviors and exploitation attempts.
Critical Alerts
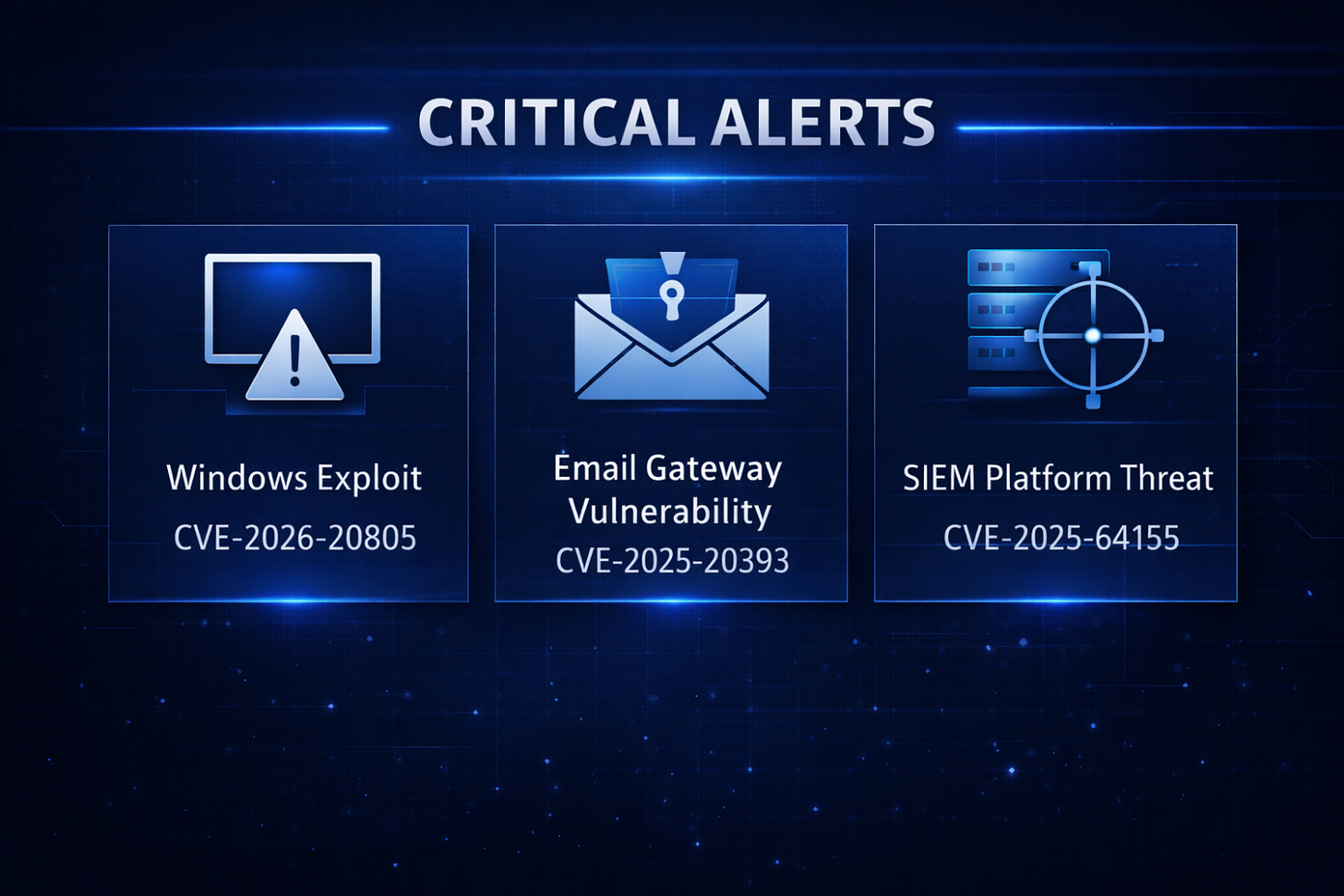
Windows exploited vulnerability (KEV-driven)
CVE-2026-20805 (Windows Desktop Window Manager) is confirmed exploited and added to CISA KEV with a federal remediation due date of February 3, 2026.
Risk: information disclosure that can enable exploit chaining and reliability improvements for follow-on code execution.
Email security appliance takeover risk (critical RCE)
CVE-2025-20393 (Cisco AsyncOS for Secure Email Gateway / Secure Email and Web Manager) is a maximum-severity remote command execution path (root-level execution) tied to active targeting.
Risk: appliance-level persistence, credential access, and visibility degradation from a compromised mail security control point.
Monitoring/SIEM platform exploitation risk (public exploit momentum)
CVE-2025-64155 (Fortinet FortiSIEM) is a critical command injection condition, with exploit code publicly available.
Risk: unauthenticated remote execution leading to root-level control of a monitoring platform, enabling both pivoting and telemetry tampering.
Threat Landscape
“Security tooling as the target”: adversaries increasingly compromise perimeter/security controls to blind defenders and harvest high-value credentials and data paths.
Rapid weaponization: public exploit publication and broad scanning compress defender response windows to days.
AI-enabled manipulation: fraud, phishing, and deepfake-assisted social engineering are now treated as top-tier business risk, especially for identity, finance, and vendor workflows.
Geopolitical lures remain effective: timely political events continue to drive credible phishing themes and payload delivery.
Technical Intelligence (IoCs, observables, and what to watch)
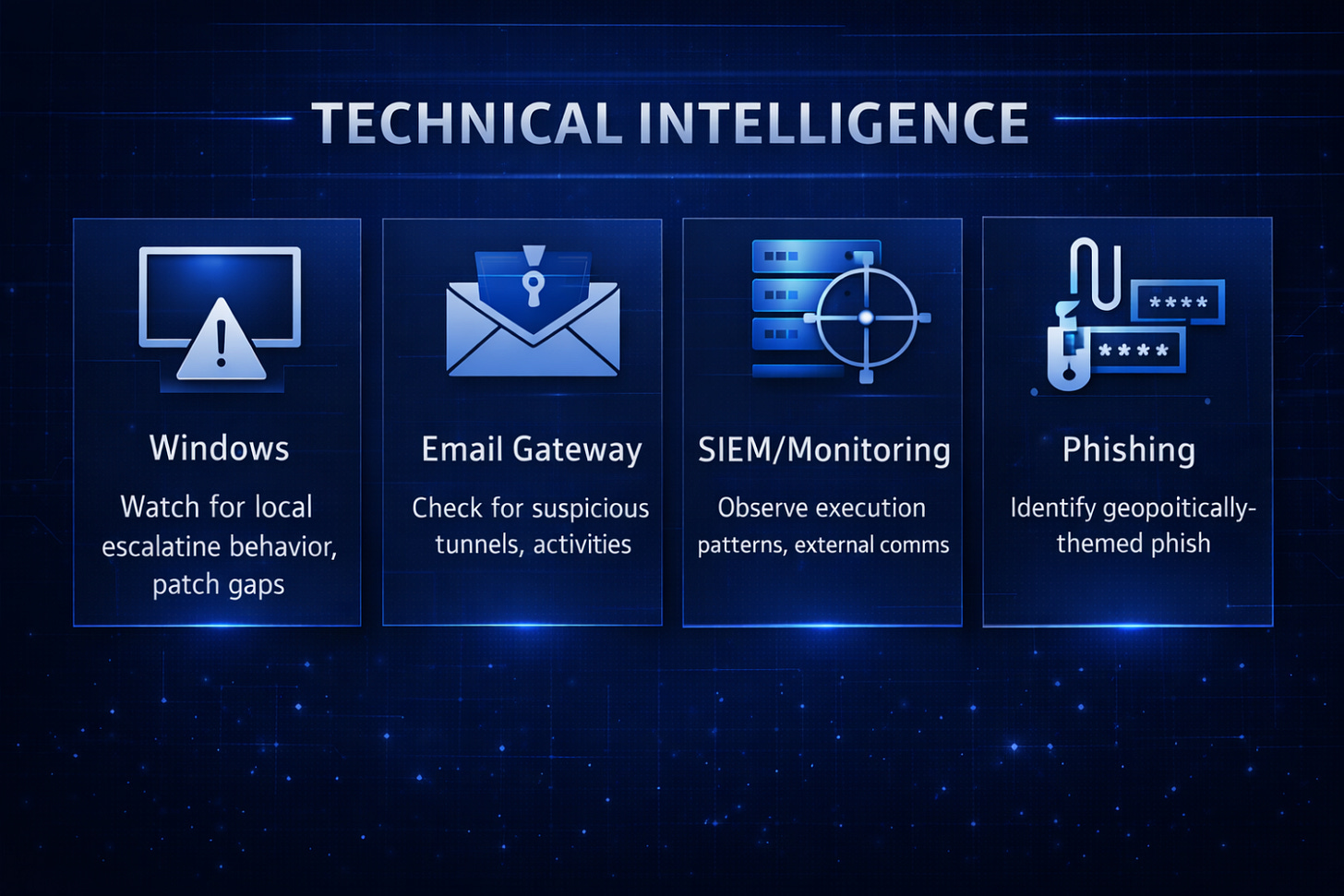
A) Windows exploitation pressure: CVE-2026-20805 (DWM) Observables to watch
Post-compromise behavior consistent with exploit chaining: credential dumping attempts, privilege escalation follow-ons, and rapid persistence establishment.
Unusual activity around patch rollout windows: new scheduled tasks, new local admins, suspicious service installs, and security control tampering.
Huntable artifacts (examples)
Endpoint activity: unexpected access patterns to credential material, LSASS interaction attempts, privilege escalation tooling, or kernel/driver-related tampering.
Defensive posture check: confirm patch coverage across VDI pools and high-churn workstation groups.
B) Cisco AsyncOS targeting: CVE-2025-20393 (Spam Quarantine feature path) High-signal observables
Unusual HTTP requests to management surfaces and quarantine-related endpoints.
Unexpected tunneling/remote access tooling presence in investigations and reports:
Configuration drift: new admin accounts, unexpected role changes, new tokens, or sudden changes to logging/export settings.
Immediate validation steps
Patch to the fixed release, then verify integrity: review admin auth logs, confirm no unauthorized persistence, and rotate credentials/tokens used to administer the appliance.
C) Fortinet FortiSIEM: CVE-2025-64155 (command injection condition) Exposure marker
Service context and network surface are frequently discussed as part of exploitation analysis (monitor service exposure is a key risk factor).
Observables to watch
Web/API patterns indicating injection attempts.
Unexpected file writes, new cron jobs, or unusual root-level processes starting shortly after inbound requests.
Unexpected outbound connections from FortiSIEM to the internet or to atypical internal hosts.
D) Active phishing tradecraft example (geopolitical lure)
Recent reporting describes phishing activity using timely geopolitical themes and archive payload delivery. Example artifact from public reporting
ZIP filename: “US now deciding what’s next for Venezuela” (archive-based lure delivery) What to watch
Inbound archive attachments with urgent geopolitical framing, newly registered or low-reputation sender infrastructure, and child-process execution from user-opened archives.
Industry Impact
Enterprises: compromise of email security or monitoring platforms creates asymmetric damage (visibility loss, credential capture, broad lateral movement).
Public sector and policy-focused organizations: elevated spearphishing pressure using geopolitical themes and rapid payload packaging.
Healthcare: breach disclosures continue to reflect delayed detection and long notification timelines, with identity data exposure driving downstream fraud risk.
Education and local government: recurring breaches highlight systemic identity and credential hygiene gaps, especially where password resets and access controls lag.
Defensive Actions
Patch and verify (do not assume):
Deploy January 2026 Windows updates broadly; confirm remediation coverage for CVE-2026-20805 across endpoints and VDI.
Patch Cisco AsyncOS appliances for CVE-2025-20393 and validate post-patch integrity.
Patch FortiSIEM per vendor guidance for CVE-2025-64155 and confirm management-plane restriction.
Reduce management-plane exposure:
Ensure admin interfaces are not internet-reachable. Require VPN + MFA + IP allowlisting for administration.
Segment security tooling networks (email gateways, SIEM, collectors, management servers) away from user LANs.
Prove the negative (assume compromise until validated):
For Cisco/FortiSIEM-class systems: review last 30 days for first-time admin logins, role changes, token creation, config exports, and anomalous outbound connections.
Rotate credentials/tokens used by administrators and integrations after patching.
Harden against AI-enabled fraud and social engineering:
Add friction to identity and finance workflows: out-of-band callback verification, dual approval for payment/vendor changes, and stricter help desk reset controls.
Monitor for deepfake/voice spoof indicators: unusual urgency, unusual channels, or mismatched verification factors.
Detection & Hunts (Sigma rules + hunts)
Sigma Rule 1: Windows execution of common tunneling utility (chisel)
title: Suspicious Tunneling Utility Execution (Chisel)
id: 1f3c7c2b-9a3e-4f3a-8a5d-0f4d8f7f4e21
status: experimental
description: Detects execution of chisel, a commonly abused tunneling utility used for covert pivoting and persistence.
author: KeysGuard OwlWatch
date: 2026-01-19
logsource:
product: windows
category: process_creation
detection:
selection_image:
- Image|endswith: '\chisel.exe'
- OriginalFileName: 'chisel.exe'
selection_cmdline:
CommandLine|contains:
- ' client '
- ' server '
- ' socks '
- ' reverse '
condition: selection_image or selection_cmdline
falsepositives:
- Authorized penetration testing
- Approved IT tunneling for troubleshooting (rare)
level: high
tags:
- attack.command_and_control
- attack.t1090 Sigma Rule 2: Linux reverse SSH tunneling behavior (ssh -R / ProxyCommand)
title: Reverse SSH Tunnel via ssh -R or ProxyCommand
id: 9b7a2e4c-3c2d-4f7e-9d3a-0c6d2b1e8f55
status: experimental
description: Detects reverse SSH tunneling often used for covert remote access and pivoting from compromised hosts or appliances.
author: KeysGuard OwlWatch
date: 2026-01-19
logsource:
product: linux
category: process_creation
detection:
selection:
Image|endswith:
- '/ssh'
- '/autossh'
CommandLine|contains:
- ' -R '
- 'ProxyCommand='
- 'ExitOnForwardFailure'
condition: selection
falsepositives:
- Approved bastion-based administration with documented tunnels
level: medium
tags:
- attack.command_and_control
- attack.t1090 Sigma Rule 3: Suspicious archive-based lure with geopolitical theme (attachment handling on endpoints)
title: Suspicious Geopolitical Lure Archive Opened (Venezuela Theme Example)
id: 2d9f8a61-1c6e-4f58-8b3b-4e7b1d2a6c90
status: experimental
description: Detects opening or handling of archive files with high-risk geopolitical lure naming patterns commonly used in spearphishing.
author: KeysGuard OwlWatch
date: 2026-01-19
logsource:
product: windows
category: file_event
detection:
selection:
TargetFilename|contains:
- 'Venezuela'
- 'US now deciding'
TargetFilename|endswith:
- '.zip'
- '.rar'
condition: selection
falsepositives:
- Legitimate research or policy work involving archives
level: medium
tags:
- attack.initial_access
- attack.t1566 Hunt Ideas (high-yield, fast execution)
Hunt 1: “Security tooling talking out”
Hunt 2: “Management-plane anomalies”
Hunt 3: “Tunneling + log clearing cluster”
Hunt 4: “Archive-to-execution chain”
Trend Analysis
Attackers are treating the security layer as a first-class target because it provides privileged execution, credential paths, and the ability to suppress alerts.
AI-enabled fraud is rising as a business risk driver, increasing the need for process controls (verification, approvals) alongside technical controls.
Exploit availability is accelerating commoditization, creating broader opportunistic exploitation beyond initial APT targeting.
Patch Priorities Priority 0 (0–24 hours)
Windows estate: validate deployment of January 2026 updates and prioritize systems with privileged access paths (IT admins, jump hosts, VDI images). Priority 1 (0–72 hours)
Cisco Secure Email Gateway / SEWM: patch AsyncOS for CVE-2025-20393; validate integrity and rotate credentials/tokens post-patch. Priority 2 (0–72 hours)
Fortinet FortiSIEM: patch for CVE-2025-64155; restrict management exposure; confirm no anomalous outbound connections or persistence. Priority 3 (this week)
OT/ICS environments: assess exposure for newly published advisories affecting industrial devices; schedule mitigation aligned to uptime constraints.
Attribution Confidence & Threat Scoring
Windows CVE-2026-20805 exploitation: High confidence (confirmed exploitation and KEV inclusion). Threat score: 8.5/10.
Cisco AsyncOS CVE-2025-20393 targeting: Medium-to-High confidence (multiple independent reports of active exploitation). Threat score: 9.2/10.
FortiSIEM CVE-2025-64155 exploitation likelihood: Medium-to-High confidence (critical severity and public exploit availability). Threat score: 8.8/10.
Spearphishing geopolitical lure activity: Medium confidence (campaign reporting is credible; impact is environment-dependent). Threat score: 7.2/10.
Playbook Updates
Security Tooling Compromise Playbook (Email Gateway / SIEM):
Patch immediately, isolate from untrusted networks, collect logs and forensic artifacts, rotate credentials/tokens, and re-baseline configuration.
Validate persistence removal: check for unauthorized users, scheduled tasks/cron, unexpected services, and outbound tunnels.
AI-Enabled Fraud Control Playbook (Identity and Finance):
Enforce dual approval and out-of-band verification for payment changes and vendor onboarding.
Tighten help desk reset workflows: verify identity using strong factors, require manager approval for high-risk accounts, and monitor for repeated reset attempts.
Sources to Monitor
CISA KEV updates and vendor advisories (Microsoft, Cisco, Fortinet)
Threat intelligence writeups on appliance exploitation and persistence tradecraft
Government/public sector incident disclosures and breach notifications
OT/ICS advisories and vendor bulletins for industrial device exposure
Executive risk reports tracking fraud, phishing, supply chain resilience, and AI security risk trends